-
Type:
Story
-
Status: Closed (View Workflow)
-
Resolution: Done
-
Affects Version/s: None
-
Fix Version/s: CFA 2020R4
-
Component/s: None
-
Labels:None
-
Sprint:CFAMX 2020R4 Sprint 5
-
SCRUM Team:Brotherhood of Mutants
-
Story Points:3
-
Work Type Classification:Sustaining
Story
As an admin, I would like a method to authorize access to APIs.
UAC
Confirm
- User permissions can be configured to control access to all API methods.
- Users can be configured to perform the some methods and not others.
- Authenticated users can be denied access to all methods for a unique API.
Updated Notes
Based on the most recent discussion with CFA about how this API will be used, we will need more than one set of Client Credentials for the various CFA apps that will use our API.
We are going to create two new users ("ahaApiUser") and security groups ("CFA AHA Application") in Inform to represent the permissions of this app. Each method on the API can then have its own permission, and we can assign those permissions to the CFA app security groups.
New Inform Users added:
ahaApiUser
cfaForecastUser
New Security groups added:
CFA AHA Application
CFA Forecast Application
New Okta application added for CFA Forecast Application:
Client Id = 0oarcorhdgYwB5rny4x6
Client Secret = -aLNYLbb68WtWf8_cjn9v4XTp5XNF9H3M1cxLWRu
(the rest of the Client Credential are the same as described in [CFAMX-11138|https://jira.hotschedules.com/browse/CFAMX-11138)
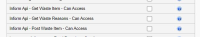
New Permissions added:
Inform Api - Get Waste Item - Can Access
Inform Api - Get Waste Reasons - Can Access
Inform Api - Post Waste Item - Can Access
And a 403 error with the message "User does not have permission to access this method."
- implements
-
CFAMX-10366 Make the Waste API robust enough for chain-wide usage by Automated Holding Assistant to inject waste data
-
- Closed
-